Decoding the hacker in 'C U Soon'
Sep. 11, 2020C U Soon is a recent Malayalam film released on Amazon Prime. The movie caught my attention especially because of the way they made this movie with minimal logistics during the COVID-19 lockdown, but still managed to justify the visuals to the narrative and the technicalities involved in the making. By far this is the only Malayalam movie which justifies the role of a cybersecurity professional a.k.a hacker character in the most believable and real manner. So let me try decoding the hacker in the movie.
The movie starts with Jimmy Kurian, the character played by Roshan Mathew, creating his dating profile on Tinder. Jimmy has enabled the Smart Photo feature on his account which I assume is the default option on signup. Tinder released this Smart Photo feature in 2016. This feature helps to shuffle/rearrange the first photo seen by others depending on the responses from other users. In simple terms, if users look at your profile, stop at let’s say the 3rd picture and swipe right, it registers as if this photo made them like you. Tinder claimed, this feature helped in 12% increase in matching during their testing. Pretty neat algorithm and there can be multiple discussion around this on the possible abuse cases. For now, let’s stick to the movie. As the story quickly progresses, Jimmy gets his match.
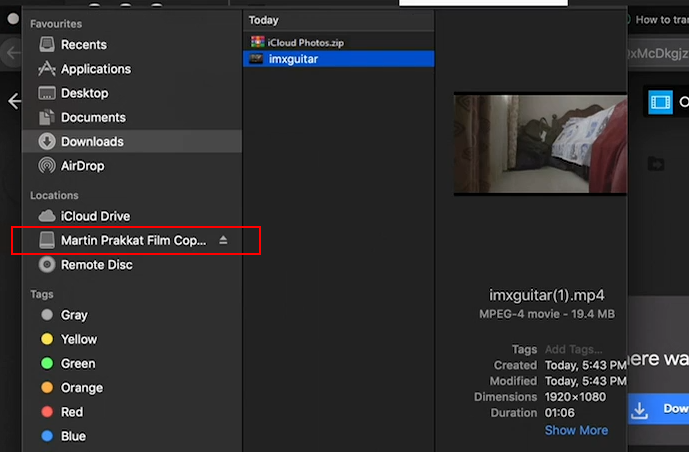
In one of the scene, Jimmy downloads a video file from the email attachment recieved from his Tinder match. The screenshot below shows the desktop screen of Jimmy’s Mac. The finder app shows an external drive connected with the device name “Martin Prakkat Film Cop…”. Martin Prakkat is an Indian writer, film director and film producer who worked in multiple Malayalam films including Theevram, Best Actor, ABCD, Charlie etc. I find it interesting to mention.
Let’s look into the hacker character in the movie - Kevin, the character played by Fahad Fasil (also the producer of the film) is the cousin brother to Jimmy. Jimmy liked a girl he met on Tinder and wanted to marry her. In one scene, Kevin uses OSINT techniques to collect information about this girl on the request of Jimmy’s mother. Kevin only had her email address to do this. Kevin would also need to get the modem details used in her house so he can try to compromise her network and get more information. This is all very practical recon stunts a real world hacker would also do. However, Kevin’s loging in to his Mac Book is interesting, his system password is only 4 characters.
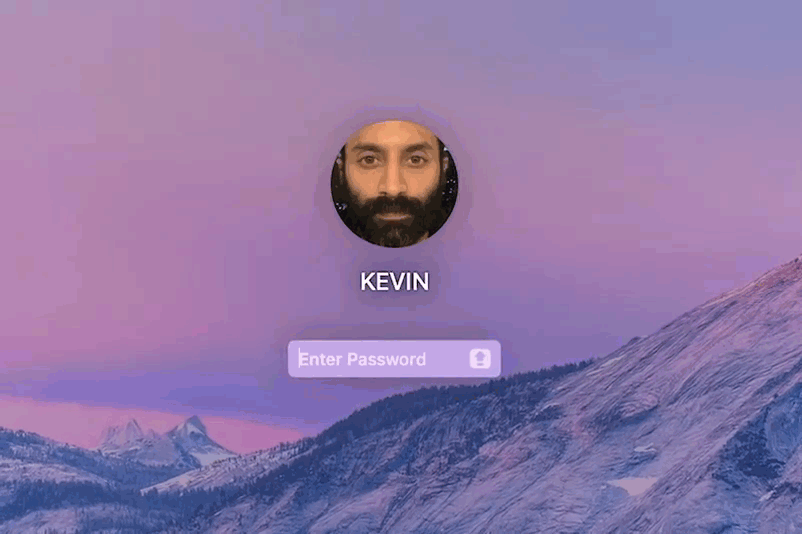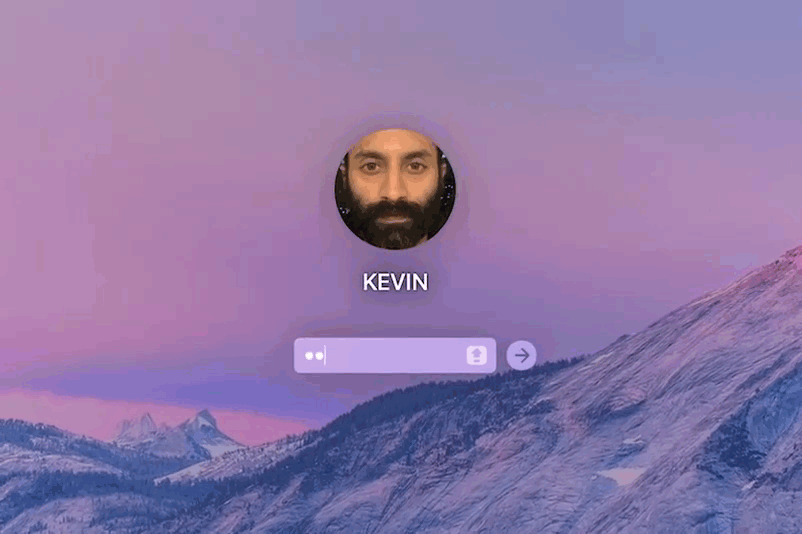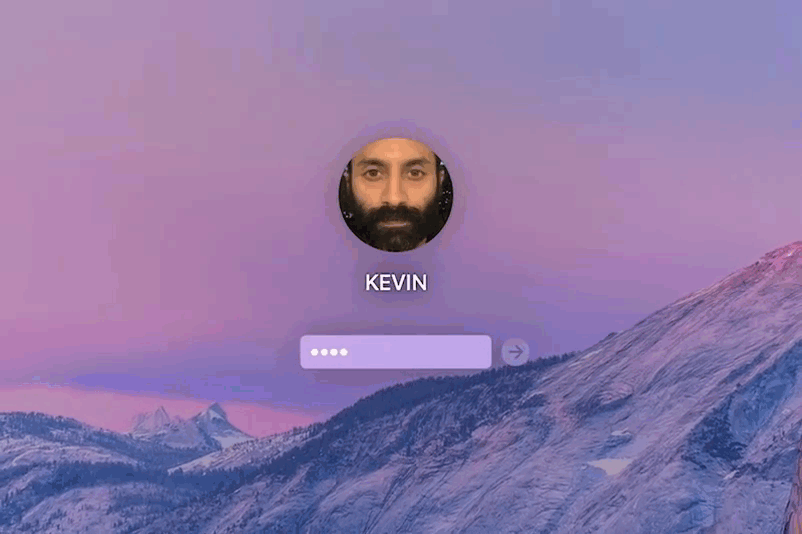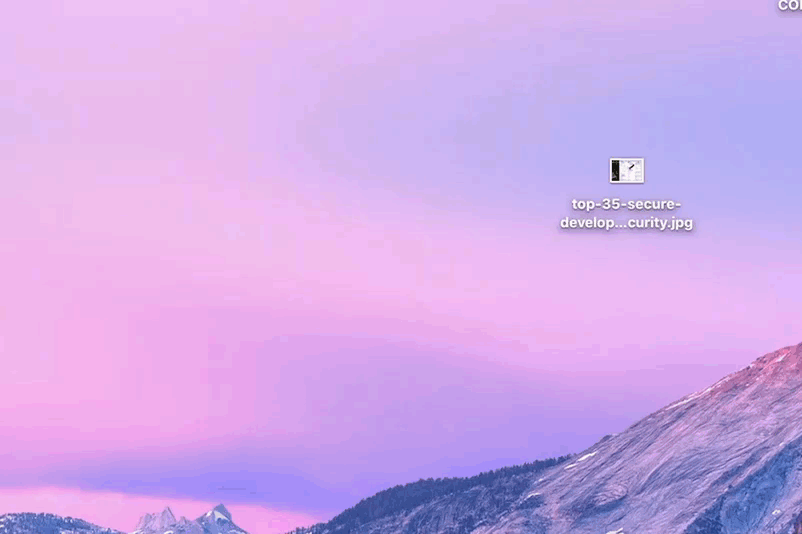
Typically someone who is professionally skilled in computer security would not take that risk of setting thier password to just 4 characters. Password cracking has become more and more easy with modern world technologies and powerful systems. For instance, a basic computer running a single AMD Radeon HD7970 GPU can try on average of an astounding 8.2 billion password combinations each second, depending on the algorithm used to scramble them. Such computational speeds were only achievable using very pricey supercomputers just a decade ago. If we upgrade the system with two or more $500 GPUs, this can achieve speeds two, three, or more times faster.
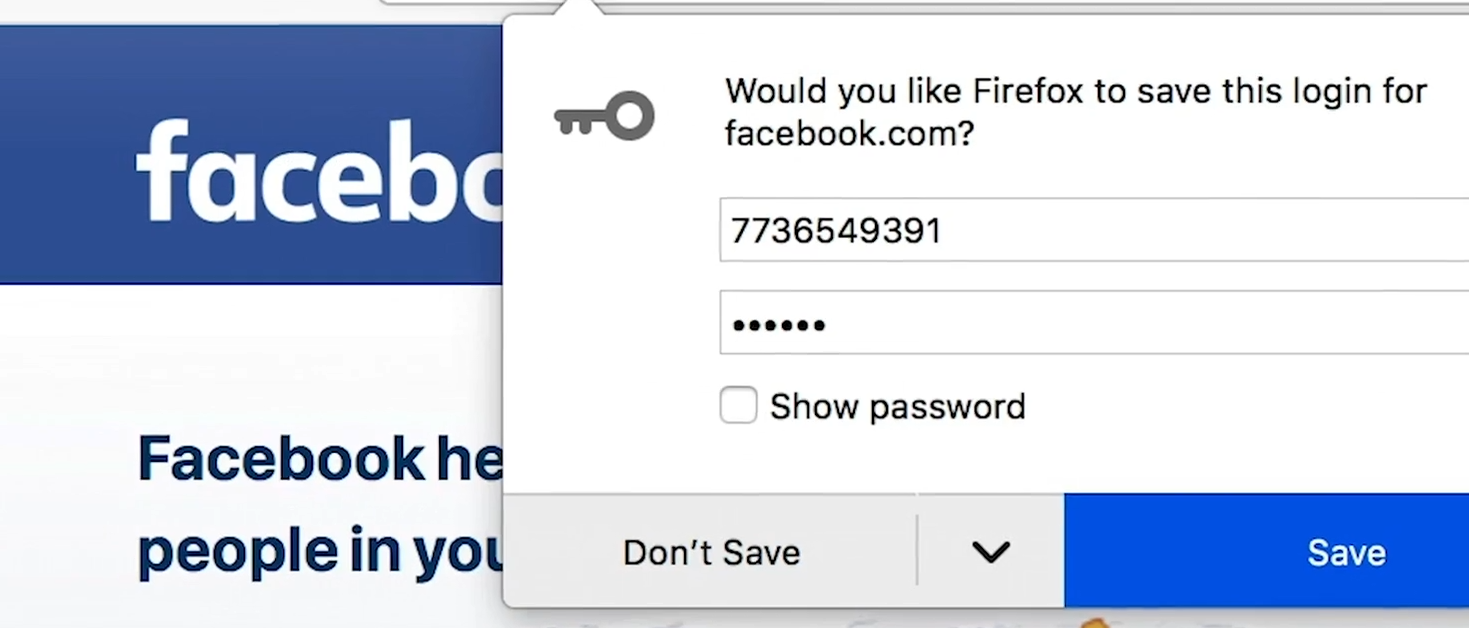
Kevin also uses just 6 characters for his Facebook account password, still not very strong password when we consider his profession.
Kevin’s desktop has some interesting files as reference to his profession.
oct-29-2012-athens-g…KOC.jpg is referring to an actual hacking incident happened in October 2012 on Greek Finance Ministry, in protest of austerity and leaked confidential data about the state of the ailing economy. References infosecurity-magazine.com, image is from alamy
command-line-conpty-1…cture.jpg is referring to the Console Architecture with Integrated ConPTY from Microsoft. Reference Microsoft devblog
In one scene, Kevin also has some sticky notes on his desktop showing good old fibonacci series programs written in C and C++.
In one of the scene, Kevin used TeamViewer to connect to Jimmy’s system and find out the modem details used in his girlfriend’s house. Once Kevin saw the information about the make and model of the modem, he then do the fancy hacking part.
In real world, if a hacker gets enough information about the target system such as the make and model, vendor and versions, etc., the actual exploitation will become easier to do. The more you know about the target, the easier to attack and compromise it. There are several public exploit databases online that regularly releases exploit codes for applications and systems. For example, Exploit-DB, Packetstorm Security, National Vulnerability Database - NVD are some of such example databses. When the hacker knows about this basic information about the target, it becomes easier to search in such public databases, know about vulnerabilities of the systems and get the suitable exploit code to execute.
The following scene shows Kevin uses Nmap, a port scanner program to find open ports and services running on the target system. Typically this is the entry point to the system and fairly the initial step in hacking.
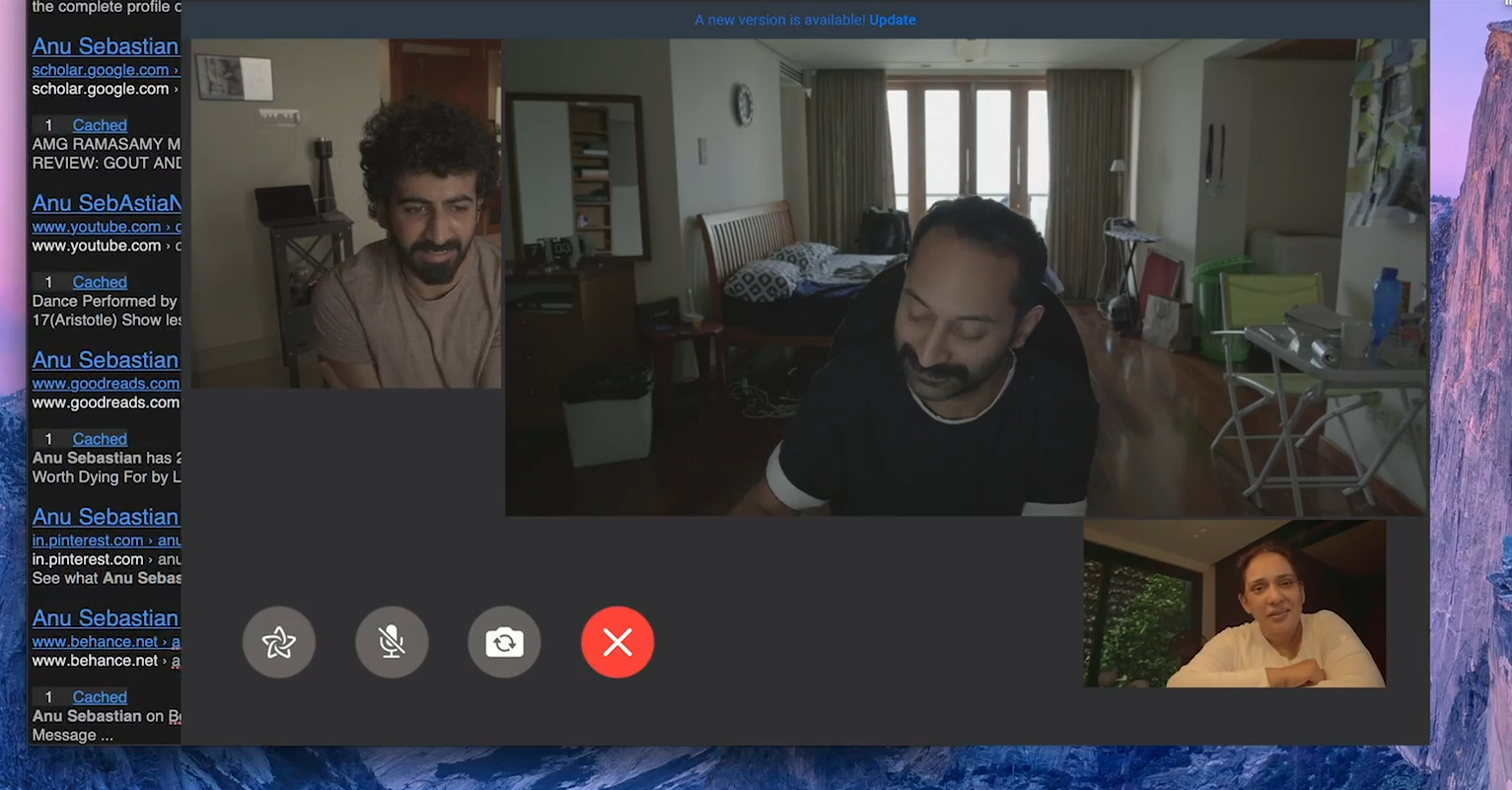
Kevin also manages to pull out her social media profiles, connected friends and family details. This is also possible to do in real life. Our social media activities are very exposed to the bad side of the internet as well. The more we expose personal life on social media, we end up victims of such profiling without even realising that we can be targeted.
On another scene, Kevin and his colleague Sanjana doing a cybersecurity presentation titled “Cybersecurity: (damn) good advice”. This is a legit presentation and published online here https://www.scribd.com/document/406021030/Cyber-Security-Presentation
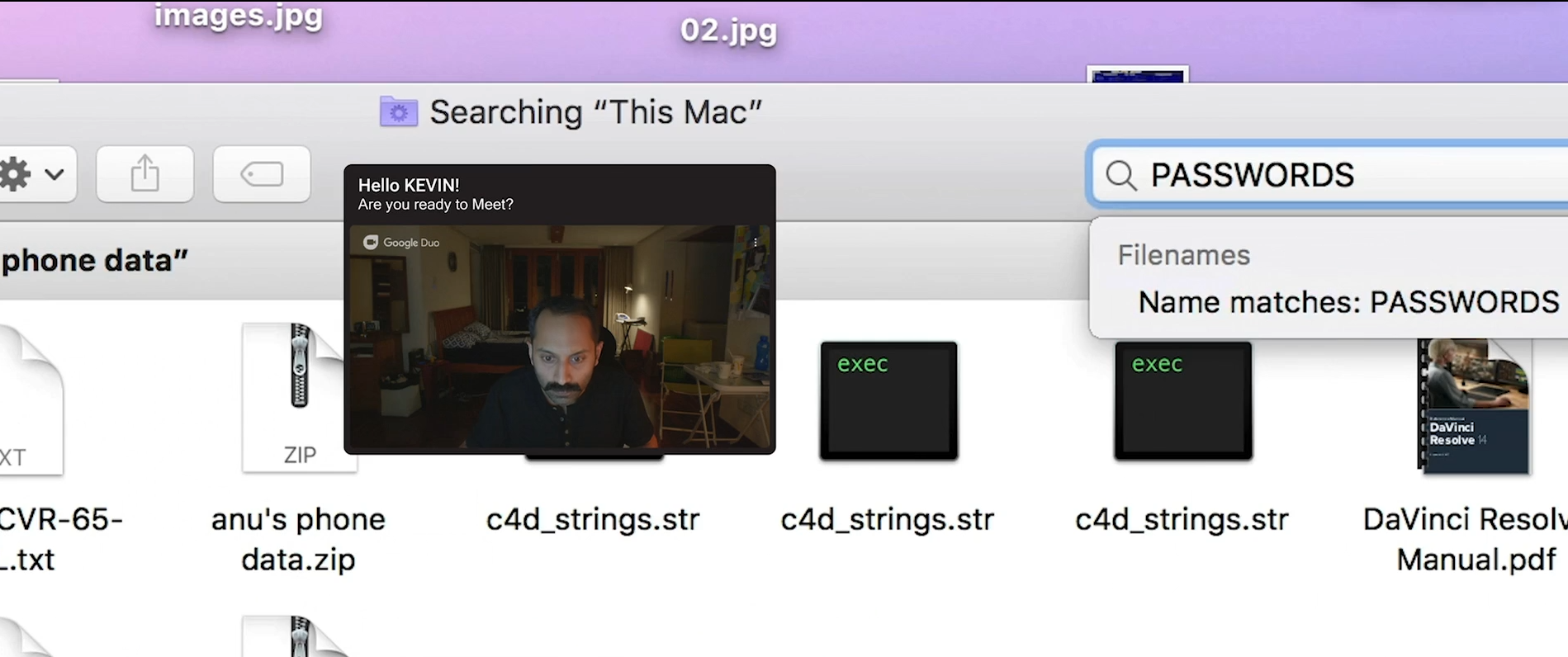
In another scene, Kevin manages to get access to the missing girl’s Facebook account. This is done by no fancy hack, but by exploiting the most common mistake most internet users do, which is storing passwwords in clear test file. Kevin searches for the keyword “PASSWORD” in the phone data and finds her Facebook password. The account did not have 2FA enabled or any restriction of access from unknown locations/devices. These are very common reasons for account compromise of most of the real social media account take over cases as well.
The brilliance in handling the logistics and making of this film surely deserves an applaud. It certainly feels good to see that movie makers are investing in quality researches and expert consultations in narrating technically challenging subjects. All credits of the images and screenshots used in this post goes to the makers of the film.